SSL Passthrough vs SSL Offloading: A Quick Primer
Approximate time to read: 9 min
SSL (Secure Socket Layer) is a widely used technology that provides secure communication over the internet. It ensures the confidentiality and integrity of data transmitted between a client and a server. Two common techniques used to handle SSL traffic are SSL Passthrough and SSL Offloading. In this article, we will explore these techniques in detail and understand the difference between them.
SSL Passthrough
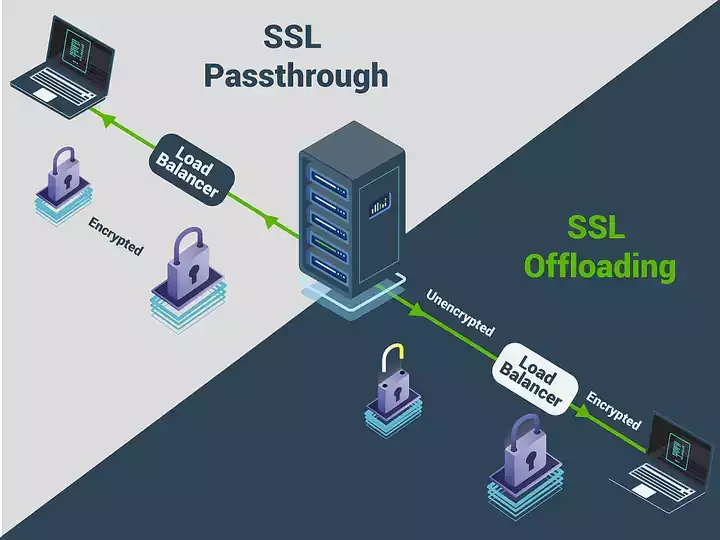
SSL Passthrough is a method where SSL encrypted traffic is forwarded directly to the backend servers without any termination or decryption at the load balancer. This means that the load balancer acts as a transparent proxy, allowing the SSL traffic to flow through it without accessing or modifying the encrypted content.
This approach is useful in scenarios where end-to-end encryption and authentication is required, and the load balancer does not need to inspect or modify SSL traffic. It provides a higher level of security and maintains the confidentiality of sensitive data.
How SSL Passthrough Works
When a client initiates an SSL connection, the load balancer intercepts the SSL handshake process and negotiates the encryption parameters with the client. Once the SSL handshake is complete, the load balancer establishes a secure connection directly with the backend server. It acts as a transparent proxy, forwarding SSL traffic without accessing or modifying the encrypted content.
This process ensures that the backend server receives the SSL traffic in its original encrypted form. The server then decrypts the SSL traffic and processes it accordingly.
One of the key advantages of SSL Passthrough is its ability to maintain end-to-end encryption. By not terminating or decrypting the SSL traffic at the load balancer, the sensitive data remains encrypted throughout the entire communication process. This is particularly important in industries such as healthcare, finance, and e-commerce, where the confidentiality of data is paramount.
Another benefit of SSL Passthrough is its simplicity. Since the load balancer does not need to handle SSL termination or decryption, it can focus solely on forwarding the encrypted traffic to the backend servers. This reduces the processing overhead on the load balancer and improves its overall performance.
However, there are also some considerations to keep in mind when implementing SSL Passthrough. Since the load balancer does not have visibility into the SSL traffic, it cannot perform tasks such as content inspection, caching, or SSL offloading. This means that any features or optimizations typically provided by the load balancer may not be available when using SSL Passthrough.
Additionally, SSL Passthrough requires careful configuration and management of SSL certificates. Each backend server must have its own SSL certificate, and the load balancer needs to be configured to trust these certificates. This can add complexity to the setup and maintenance of the SSL infrastructure.
In conclusion, SSL Passthrough is a method that allows SSL encrypted traffic to be forwarded directly to backend servers without termination or decryption at the load balancer. It provides end-to-end encryption and maintains the confidentiality of sensitive data. However, it may limit the load balancer’s ability to perform certain tasks and requires careful management of SSL certificates.
SSL Offloading
SSL Offloading, also known as SSL termination or SSL decryption, is a technique where SSL traffic is decrypted at the load balancer and then forwarded to the backend servers as unencrypted HTTP traffic. This allows the load balancer to perform various operations on the HTTP payload, such as load balancing and content inspection. This approach provides advantages in terms of performance and scalability. By offloading the SSL decryption process to the load balancer, the backend servers are relieved of the computationally intensive task of handling SSL encryption and decryption. This results in improved server performance and increased throughput.
How SSL Offloading Works
When a client initiates an SSL connection, the load balancer intercepts the SSL handshake process and negotiates the encryption parameters with the client, just like in SSL Passthrough. However, in SSL Offloading, the load balancer acts as the SSL endpoint, terminating the SSL connection and decrypting the SSL traffic.
Once the SSL connection is terminated, the load balancer forwards the decrypted traffic to the backend servers as unencrypted HTTP traffic. The backend servers then process the HTTP traffic as if it was received over a regular HTTP connection.
SSL Termination
SSL Termination is similar to SSL Offloading in that SSL traffic is decrypted at the load balancer. However, in SSL Termination, the load balancer establishes a new SSL connection with the backend servers, re-encrypting the traffic before forwarding it.
This approach is useful when there is a need to maintain end-to-end encryption between the client and the backend servers, while still allowing the load balancer to perform operations on the decrypted traffic.
How SSL Termination Works
Like SSL Offloading, SSL Termination begins with the load balancer intercepting the SSL handshake process and negotiating the encryption parameters with the client. Once the SSL connection is terminated, the load balancer decrypts the SSL traffic.
However, instead of forwarding the decrypted traffic in its unencrypted form, the load balancer establishes a new SSL connection with the backend servers and re-encrypts the traffic. This ensures that the traffic between the load balancer and the backend servers remains secure.
The backend servers process the re-encrypted SSL traffic and respond accordingly. The load balancer then receives the response, decrypts it, and forwards it back to the client over the initial SSL connection.
Exploring High Availability Load Balancing
In addition to handling SSL traffic, load balancers also offer high availability capabilities, ensuring that applications and services remain accessible even in the presence of failures or increased traffic. High Availability Load Balancing distributes incoming traffic across multiple backend servers, maximizing resource utilization and providing redundancy.
Implementing High Availability Load Balancing involves deploying multiple load balancers in a distributed architecture. These load balancers work together to distribute the traffic and ensure that it is directed to healthy backend servers.
By effectively distributing the load, High Availability Load Balancing improves the overall performance and responsiveness of the application, enhancing the user experience.
Ensuring Seamless Performance with High Availability Load Balancing
To ensure seamless performance with High Availability Load Balancing, it is important to configure the load balancers to monitor the health of the backend servers. This can be done through various health check mechanisms, such as sending periodic requests to the servers and checking for valid responses.
If a backend server fails or becomes unresponsive, the load balancer automatically detects it and stops forwarding traffic to the affected server. This allows the remaining healthy servers to handle the traffic, maintaining the availability and continuity of the service.
SSL Termination vs SSL Offloading: What’s the Difference?
SSL Termination and SSL Offloading are two similar techniques that involve decrypting SSL traffic at the load balancer. The main difference between them lies in how the load balancer handles the decrypted traffic.
In SSL Termination, the load balancer establishes a new SSL connection with the backend servers, re-encrypting the traffic before forwarding it. On the other hand, in SSL Offloading, the load balancer forwards the decrypted traffic as unencrypted HTTP traffic.
The choice between SSL Termination and SSL Offloading depends on the specific requirements of the application or service. SSL Termination is recommended when end-to-end encryption is desired, while SSL Offloading is suitable when the load balancer needs to perform operations on the decrypted traffic.
SSL Termination vs SSL Passthrough: What’s the Difference?
SSL Termination and SSL Passthrough are two distinct methods of handling SSL traffic. While both techniques involve passing SSL traffic through the load balancer, they differ in how the load balancer interacts with the SSL traffic.
In SSL Termination, the load balancer terminates the SSL connection, decrypts the traffic, and establishes a new SSL connection with the backend servers. SSL Passthrough, on the other hand, allows SSL traffic to flow through the load balancer without any termination or decryption.
The choice between SSL Termination and SSL Passthrough depends on the specific requirements of the application or service. SSL Termination provides the load balancer with the ability to perform operations on the decrypted traffic, while SSL Passthrough maintains end-to-end encryption and is useful when the load balancer does not need to access or modify the SSL traffic.
Securing Data Transmission with SSL Termination
SSL Termination plays a crucial role in securing data transmission between clients and servers. By decrypting the SSL traffic at the load balancer, it allows the load balancer to inspect and analyze the content for security threats, such as malicious code or unauthorized access attempts.
Furthermore, SSL Termination provides an additional layer of protection by enabling the load balancer to enforce security policies, such as restricting access based on client certificates or applying web application firewalls.
Overall, SSL Termination enhances the security posture of the system and ensures the confidentiality and integrity of data during transmission.
Securing Data Transmission with SSL Passthrough
SSL Passthrough is another method of securing data transmission between clients and servers. By allowing SSL traffic to flow through the load balancer without termination or decryption, SSL Passthrough ensures end-to-end encryption and maintains the confidentiality of sensitive data.
This approach is useful in scenarios where the load balancer does not need to access or modify the SSL traffic. It provides a higher level of security by preventing any potential points of vulnerability that may be introduced during the SSL termination process.
However, it is important to note that SSL Passthrough does not provide the load balancer with the ability to inspect or analyze the encrypted traffic for security threats. Additional security measures, such as network intrusion detection systems, may be required to complement SSL Passthrough.
Conclusion
In conclusion, SSL Passthrough and SSL Offloading are two techniques commonly used to handle SSL traffic. They serve different purposes and offer unique benefits depending on the specific requirements of the application or service.
SSL Termination, on the other hand, combines the advantages of both techniques, allowing the load balancer to perform operations on the decrypted traffic while maintaining end-to-end encryption. Understanding these techniques and their differences is crucial in choosing the most appropriate approach for securing data transmission and optimizing application performance.
Understanding the nuances of SSL Passthrough and SSL Offloading is just the beginning of optimizing your cloud applications. With Quotaguard, you get an static IP infrastructure platform as a service tailored to your needs, complete with world-class support for a variety of programming languages and frameworks. Don’t let the complexities of SSL configurations slow you down. Sign up at Quotaguard today and experience resilient static IP solutions, built for your cloud deployments.